This is the ORIGINAL post.
When you create an AWS Lambda function without associating it with a Virtual Private Cloud (VPC), it runs in the default Lambda network configuration, which means it operates outside of any VPC.
This might be most of your cases but sometimes, we do need to associate lambda function within our VPC as we have an EC2 instance or RDS instance that requires a private connection.
It is easy to set up the VPC association for the lambda function and to connect to the instance in your VPC, you just need to properly allow the outbound traffic to the services within your VPC via IP/Port no matter what subnets associated with your function are.
However, if your Lambda Function requires an internet connection, that will be a different story.
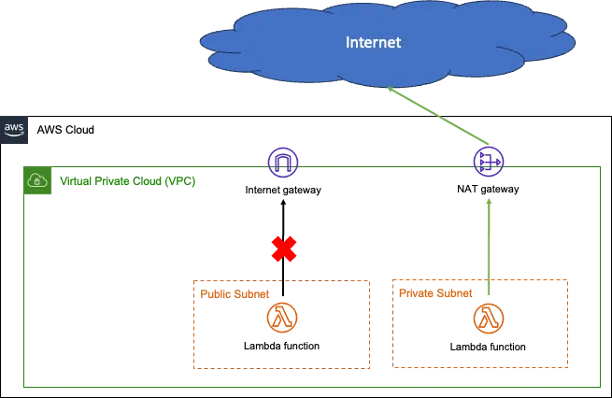
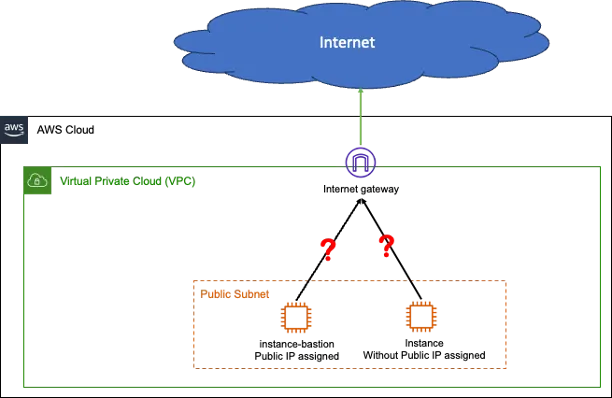
From the diagram above, the Lambda function placed in Public subnet still cannot access to public internet. You have to place the Lambda function into a Private subnet with a direct route to a NAT device so that your function can access the public internet.
Let’s have a look at how AWS defines a Public subnet and a Private subnet.
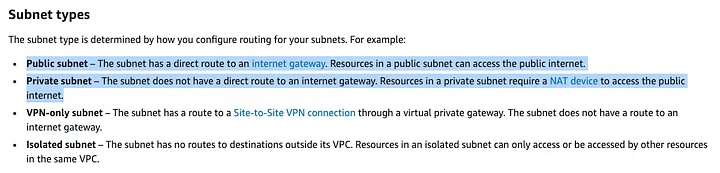
Then in the Lambda function, the description of Internet and service access for VPC-connected functions is like this:
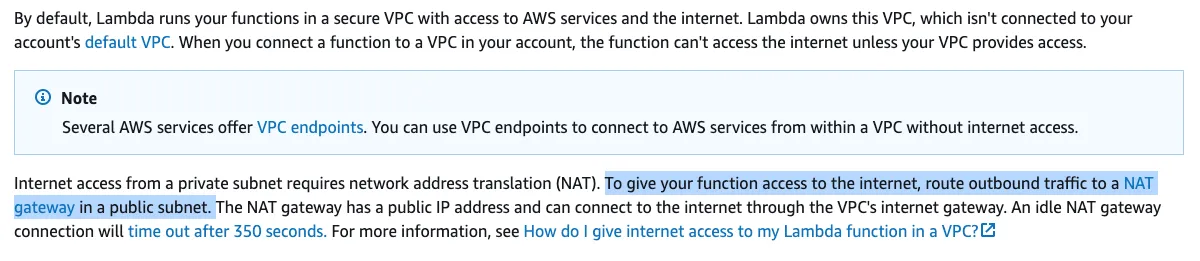
NAT gateway in a public subnet? It is so confusing, right?
Now let me tell you why Lambda Function placed in a Public Subnet still cannot connect to the public internet.
The Answer is Lambda function is not assigned with a public IP when it is associated to your VPC!!!
I did not find any document illustration this on AWS but if you see it some where, please leave the URL in the comments. Thank you.
Demo
Now, let’s go through a demo that you can follow along to better understand how the networking works.
Let’s create a New VPC first with two public subnets and two private subnets. Public subnets have a direct route to the Internet gateway and Private subnets have a direct route to NAT gateways.
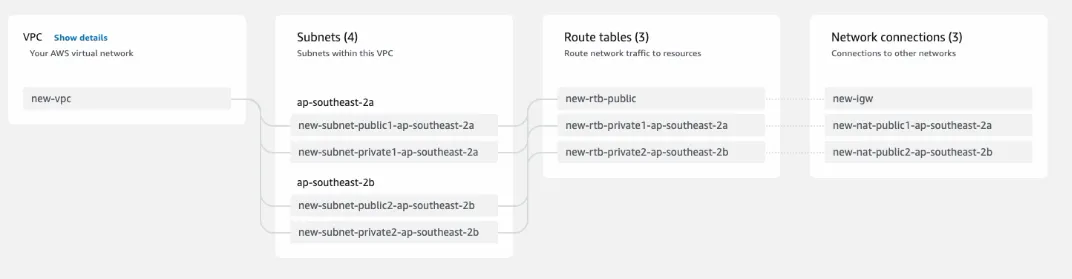
Then we create a Lambda function and associate it to these two public subnets.
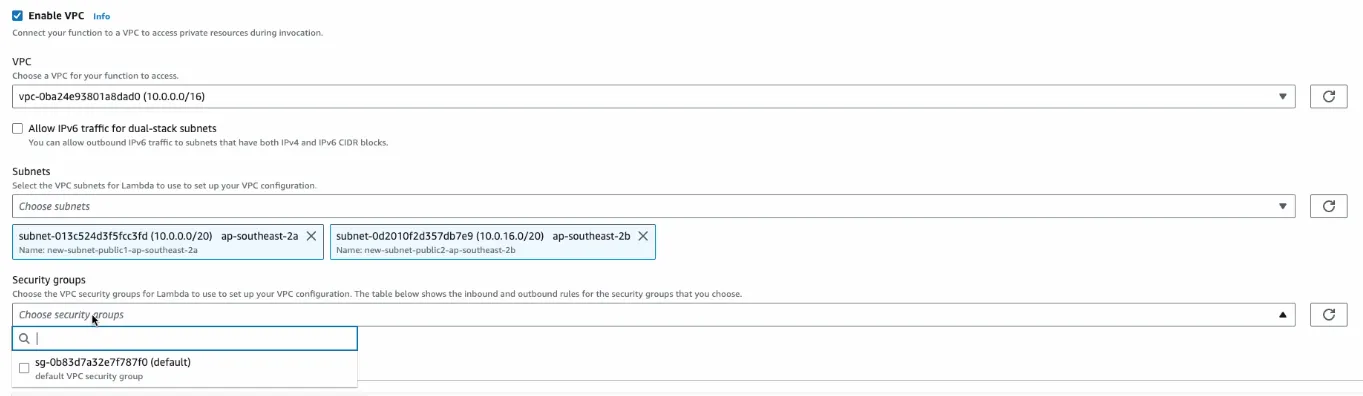
We use Python as the Lambda Runtime and the code is as below:
import socket
def lambda_handler(event, context):
try:
socket.create_connection(("8.8.8.8", 53), timeout=20)
return {"statusCode": 200, "body": "Internet connection is available!"}
except Exception as e:
return {"statusCode": 500, "body": f"Error checking internet connection: {str(e)}"}
Then we do our first test and we get Connection Timeout.

Then we switch the subnets to the two Private subnets.
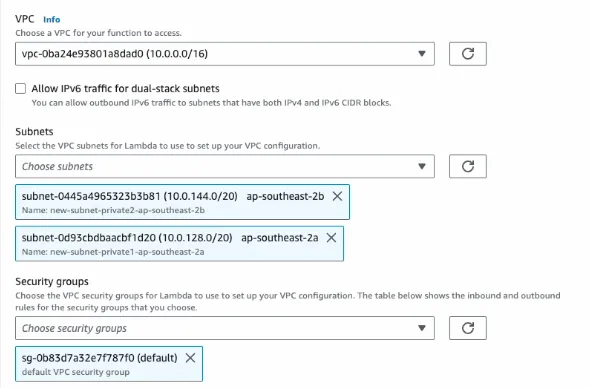
Run the test again. The Internet connection is now available!
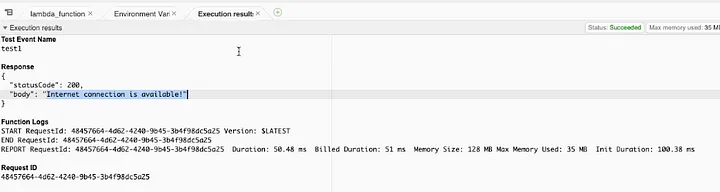
So now we know the conclusion, Lambda function has to rely on the NAT Gateway if you associate it to a VPC!!!
If you are interested in doing some experiments by yourself, you can try below and see if an EC2 instance without Public IP assigned can access the public internet. Remember, you need to connect to the non-IP instance via the Bastion Instance
Finally
Please follow me on Medium if you are interested in Cloud, DevOps, automation, programming, and any tech topics. I would also appreciate it if you could give me a clap.
Your comments are always welcome.
Thanks.







